Enterprise-Grade PTaaS, Not Just for Enterprises
Build a scalable, compliant, resilient security program with pentesting as a service

Supercharge Your Security Pen Testing Compliance
Ad-hoc, one-time pentests don’t cut it anymore. You need continuous pentesting for proactive security and compliance. And you cannot allow cost or resources to become roadblocks to building a strong cybersecurity framework.
With Siemba’s PTaaS platform, and its range of powerful features, you don’t have to.
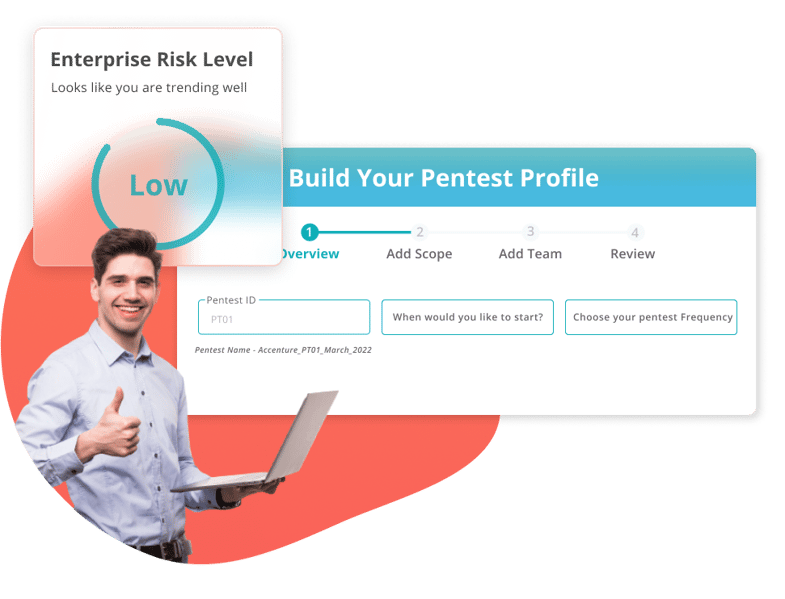
Repeatable & Scalable
Constantly challenge your security posture
Test and secure your business-critical assets at scale with pentests that you set up once and repeat automatically at desired frequencies.

Reports & Dashboards
Say good-bye to multiple emails, PPTs and reports
Everybody knows where everything is, at all times. Keep your stakeholders in the loop and showcase compliance with custom dashboards and up-to-date reports.
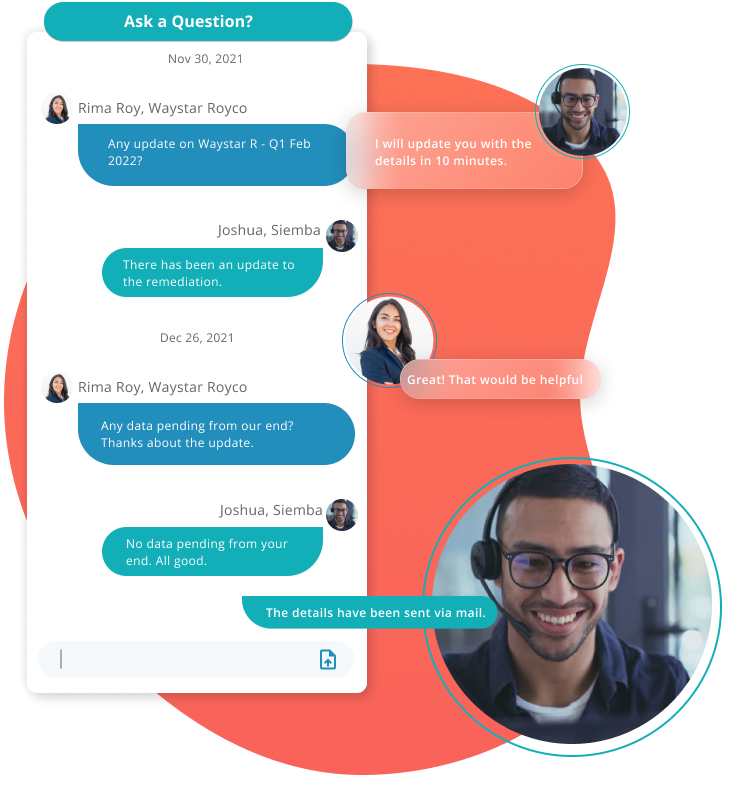
Responsive Teams
Work with a testing team that doesn’t ghost you
Communicate with the testing team, ask queries and get detailed answers quickly; with the in-built chat module.
Pentesting Made Painless
We understand that pentesting is a key aspect of your cybersecurity. But just because it’s business-critical doesn’t mean it should be difficult. It’s time to transform your pentesting process.
From Chaotic
- 15 - 20 Days to start a Pentest
- 90 Days before you see the result
- 100+ Calls, meetings and emails to understand your test results
To Compliant
- 60 Mins to set up a pentest
- Start seeing test results in near real time
- In-depth, issue-level visibility to start remediation
From Reactive
- Piece-meal, point-in-time pentesting
- No insights into risk landscape
- Reactive remediation measures
To Resilient
- Scheduled recurring pentests for all assets
- Enterprise-level visibility of risk landscape
- Proactively improve security posture
We are with you at every step
Our team of experts is here to take you through a detailed demo of the Siemba PTaaS platform, and showcase exactly how it can transform your security posture.
Pentesting Made Powerful
Cybersecurity threats don’t discriminate. Slow and cumbersome point-in-time assessments are just not enough. If you are a start-up or mid-size, your pentesting needs scale. If you're an enterprise, your pentesting program needs repeatable processes, scale, and visibility.
And all of that is possible with Siemba’s enterprise-grade PTaaS platform.

Engineered for Scale
Whether you have 2 apps, 200, or even 2000 apps to test, Siemba’s PTaaS platform is built to handle rigorous pentesting at scale.

Designed for Compliance
Demonstrate continuous compliance to your clients and investors with always up-to-date pentest results.
.png?width=958&height=570&name=graphic%203%20pentest%20(1).png)
Built for Visibility
Enable seamless visibility into your real-time risk and remediation pipeline; for the CISO, for your developers, and everyone in between
Clients Who Believe in Us
“As a Lead and Demand Generation platform, Leadlytics Labs processes several hundred thousands of confidential data points on behalf of our customers every month. Siemba helps us keep our data and business secure with their 24*7 Siemba Ops Program. The team at Siemba has been an absolute pleasure to work and continuously strives to add value.”
Tested by the Best
No crowd sourcing, no outsourcing. Only certified, experienced pentesters on the Siemba team to work on your business-critical applications.

AWARDS

2019 TOP 200 MSSPs

2020 TOP 250 MSSPs

2021 TOP 200 MSSPs
Discover How the Siemba PTaaS Platform Can Work for You
Get a low-down on pentesting as a service, and how Siemba platform can deliver enterprise-grade PTaaS for your business.
_updated.png?width=6725&height=2157&name=Siemba-1%20(3)_updated.png)
