AISO – Your Always-On
AI Security Officer
.webp?width=2000&name=banner%20(1).webp)
Turn Data Overload Into Decision-Ready Insights
Too much security data, not enough action? AISO by Siemba transforms complex vulnerability and threat data into clear, strategic insights, automatically. Sitting across the entire CTEM platform, AISO delivers prioritized, contextual, and actionable intelligence to help security leaders, teams, and stakeholders stay ahead of threats and aligned on what matters most.
Data Isn’t the Problem-Context Is
Turn data overload into decision-ready insights

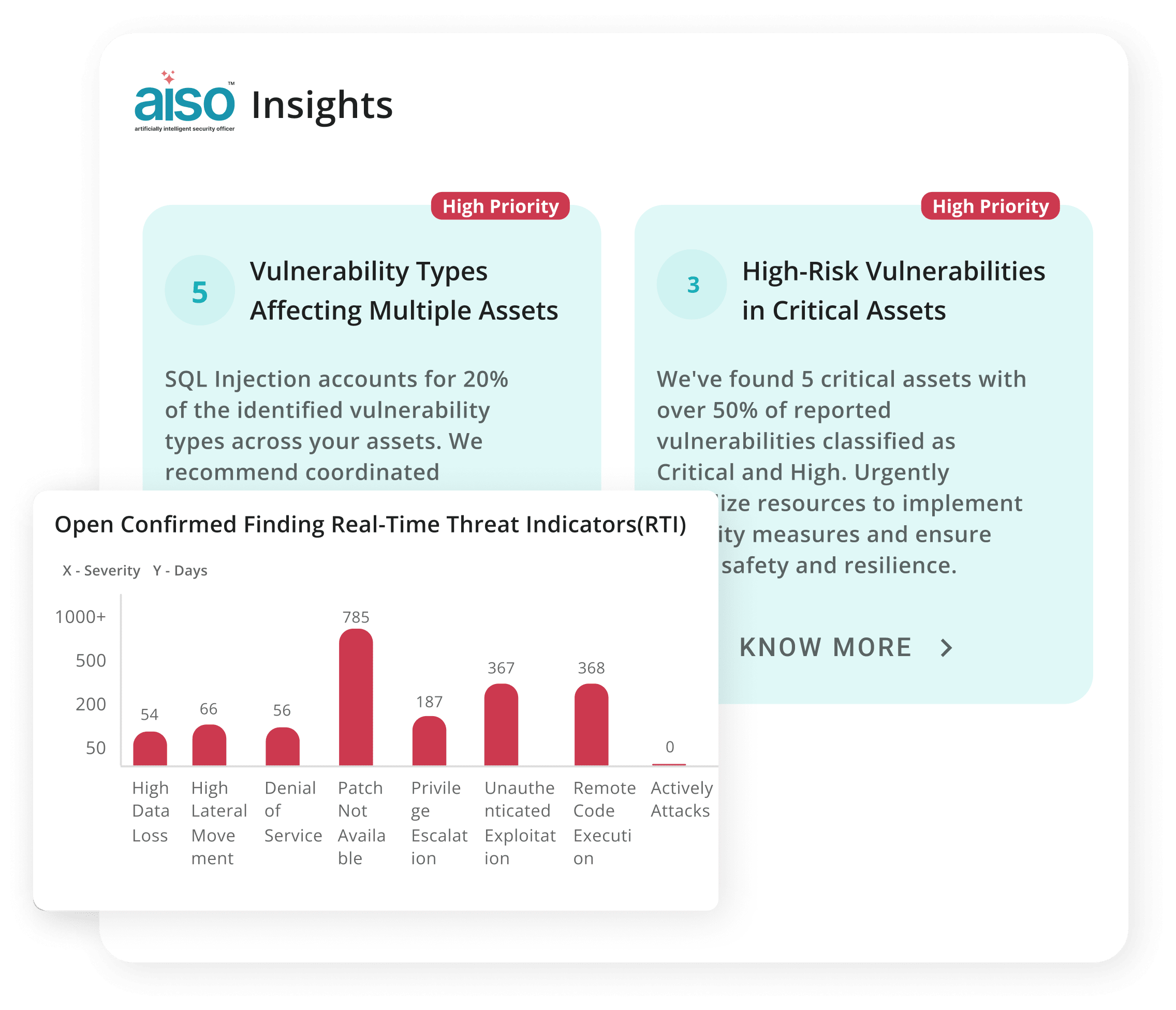
Analysis
Paralysis
Mountains of raw data, but no real way to filter noise from signal, or drive meaningful action.

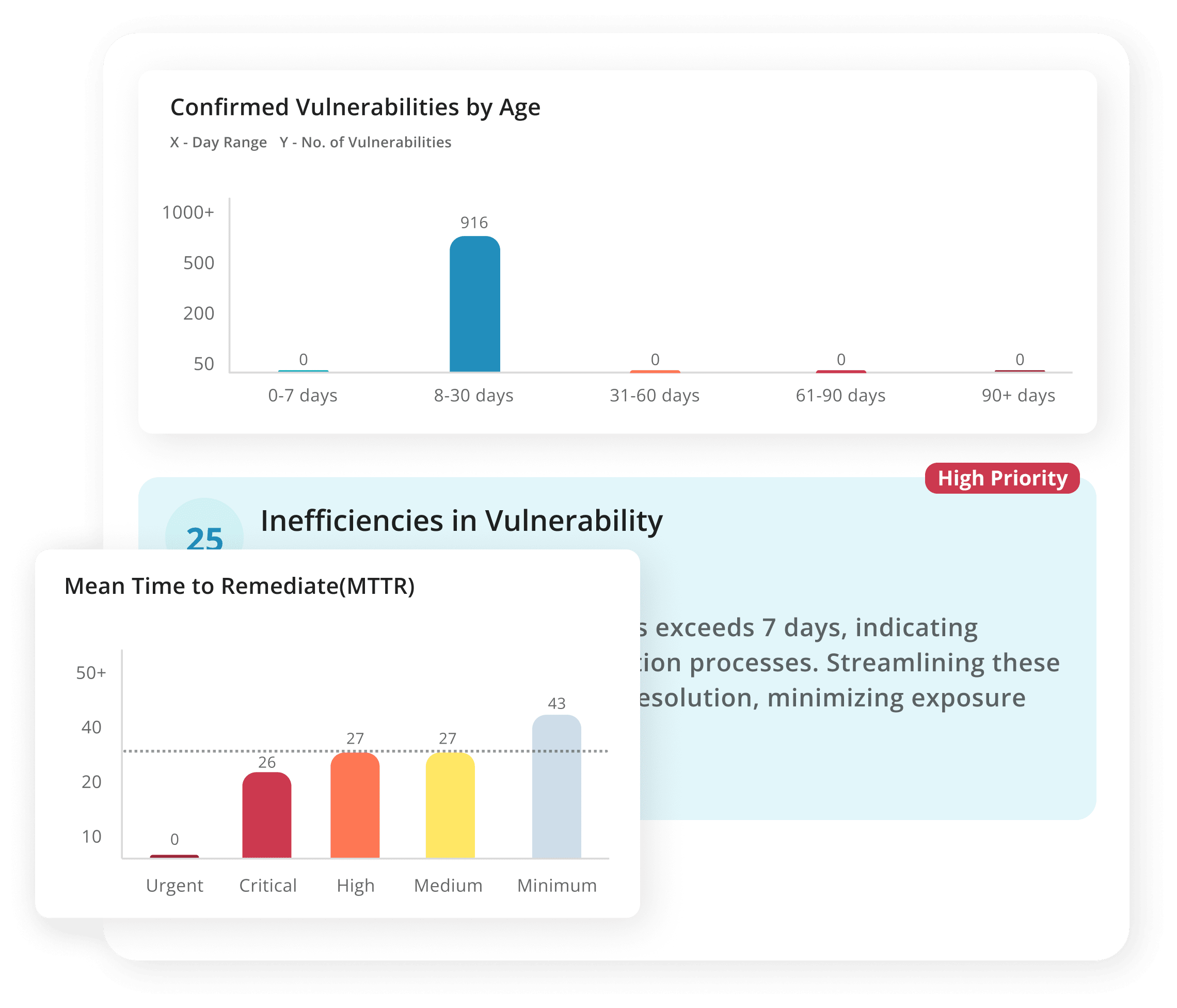
Slow Decision-
Making
Manual correlation and fragmented insights mean leadership operates on lagging indicators, not real-time threats.

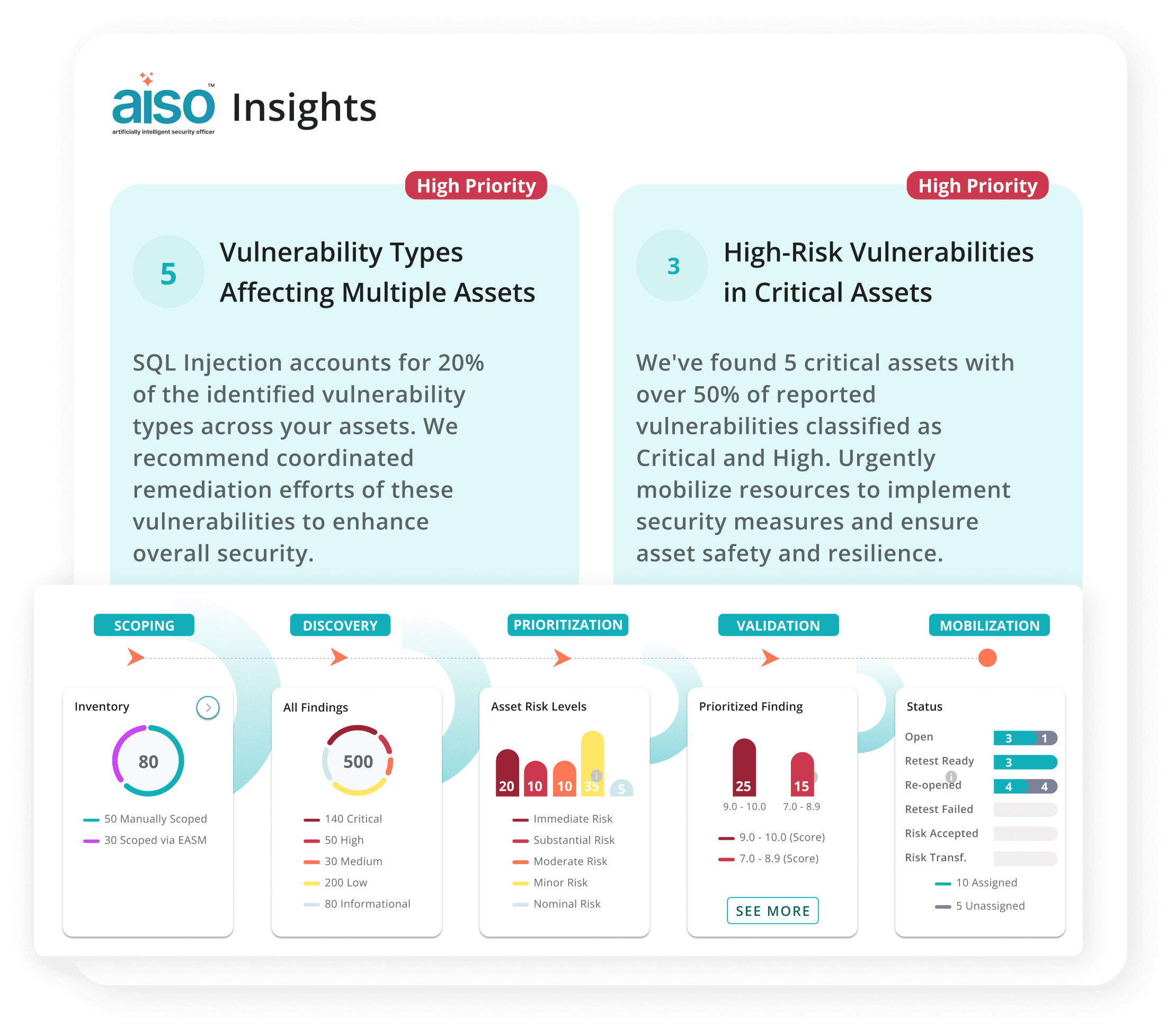
Disconnected
Tools
Insights, if at all available, live in silos across platforms. There’s no single place to view your CTEM, EASM, VA, GenPT, and PTaaS posture.

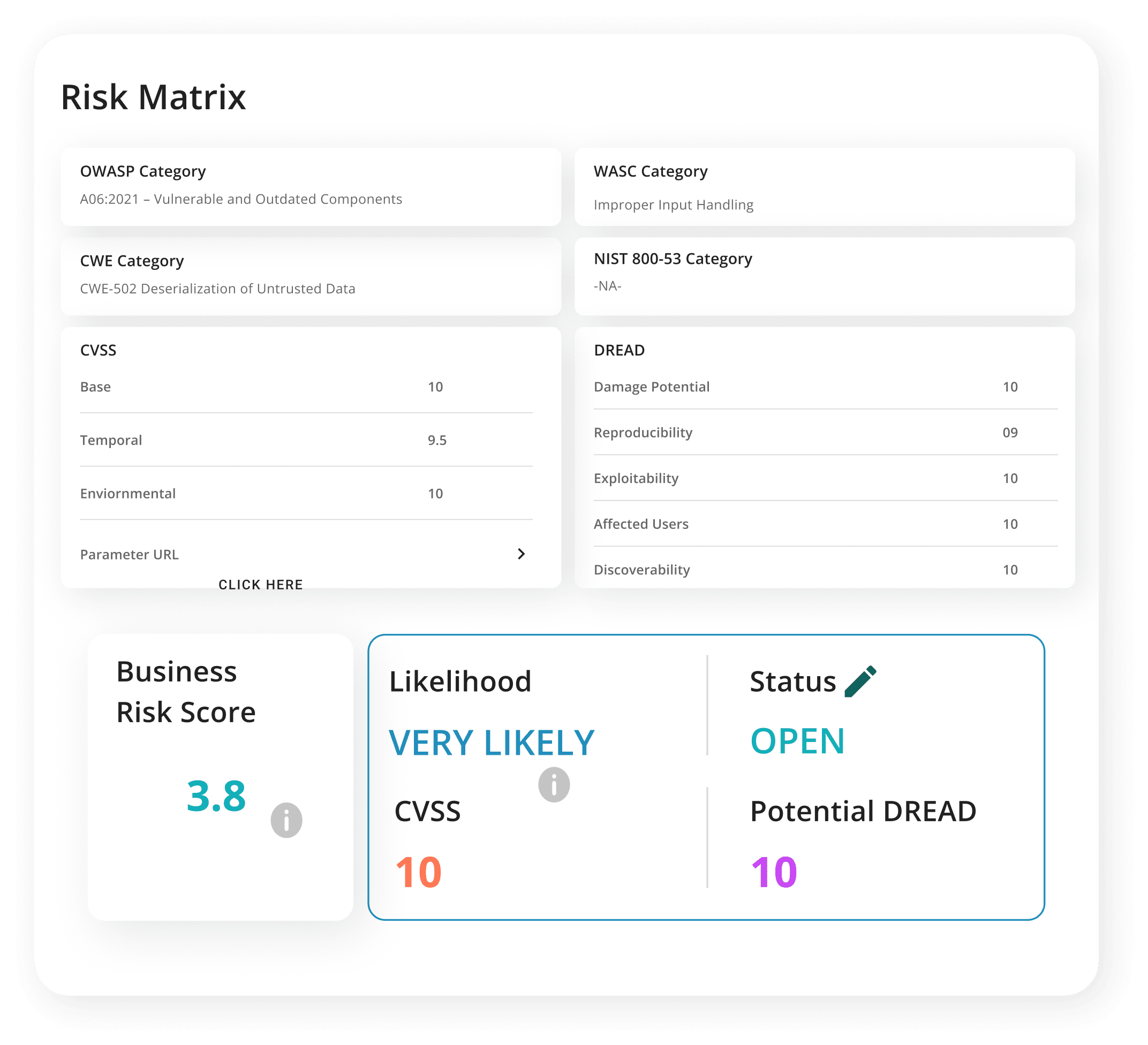
No Executive
Translation
Security data is often too technical or too vague, leaving CISOs and boards struggling to get clarity.
Smarter Decisions. Faster Actions. Stronger Posture.
Smarter Decisions. Faster Actions. Stronger Posture.

-3.webp)

Traditional Security Reporting vs. Siemba’s AISO
Capability |
Traditional Approach |
Siemba AI-Driven CTEM |
|---|---|---|
|
Insight Generation
|
Manual review, isolated reports
|
AI-driven, real-time insights across all Siemba modules
|
|
Threat Prioritization
|
Focus on severity levels
|
Prioritizes based on exploitability, patchability,
exposure, asset risk, threat intelligence & business impact |
|
Efficiency Analytics
|
Manual MTTR and trend reports
|
Automatic tracking of MTTR, vulnerability age, and
remediation gaps |
|
Cross-Team Visibility
|
Disconnected tools and dashboards
|
Unified platform aligned with CTEM, EASM, VA, GenPT, PTaaS
|
|
Compliance Readiness
|
Tedious mapping to frameworks
|
Built-in compliance tagging (NIST, PCI, MITRE, OWASP, etc.)
|
|
Reporting
|
Cumbersome, requires heavy lifting
|
One-click reports tailored for SecOps teams, executives,
developers and compliance teams |
How Your Teams Use AISO
AISO Is the Brain Behind Your Security Operations
Seamlessly embedded across every Siemba module, AISO is the connective tissue that turns raw security data into real security intelligence.
Activate AISO & stop drowning in data.
Start leading with insight.
Ready to meet your new AI Security Officer?



