See What Attackers
See – Before They Strike
.png?width=1171&height=766&name=banner%20(1).png)
Siemba’s AI-Driven External Attack Surface Mapping (EASM)
Your attackers don’t need permission to scan your environment—so why should you? Siemba’s EASM capability provides a real-time, non-intrusive view of your external-facing assets exactly the way threat actors see it. Discover hidden exposures, misconfigurations, and weak spots across your digital
perimeter, and act before they become breach points.
Trusted by






Why Traditional Discovery Tools Can’t Keep Up
Legacy methods miss the mark on external risk
Blind Spots Everywhere
Legacy scanners require manual input and credentials, leaving unknown or orphaned assets out of scope and invisible
Fragmented Data
Point solutions give siloed, static results. There’s no unified view of your domains, subdomains, TLS configurations, or external risks
No Continuous Monitoring
Periodic scans can’t keep up with cloud-scale asset changes and evolving threats, leading to stale risk data
Zero Actionability
Most tools highlight issues but offer no deeper testing, prioritization, or guidance, leaving your teams stuck in triage

Why Traditional Discovery Tools Can’t Keep Up
Legacy methods miss the mark on external risk
Blind Spots Everywhere

Legacy scanners require manual input and credentials, leaving unknown or orphaned assets out of scope and invisible
Fragmented Data
Point solutions give siloed, static results. There’s no unified view of your domains, subdomains, TLS configurations, or external risks
No Continuous Monitoring

Periodic scans can’t keep up with cloud-scale asset changes and evolving threats, leading to stale risk data
Zero Actionability
Most tools highlight issues but offer no deeper testing, prioritization, or guidance, leaving your teams stuck in triage
All the Visibility. None of the Guesswork.
What makes Siemba’s EASM a game-changer
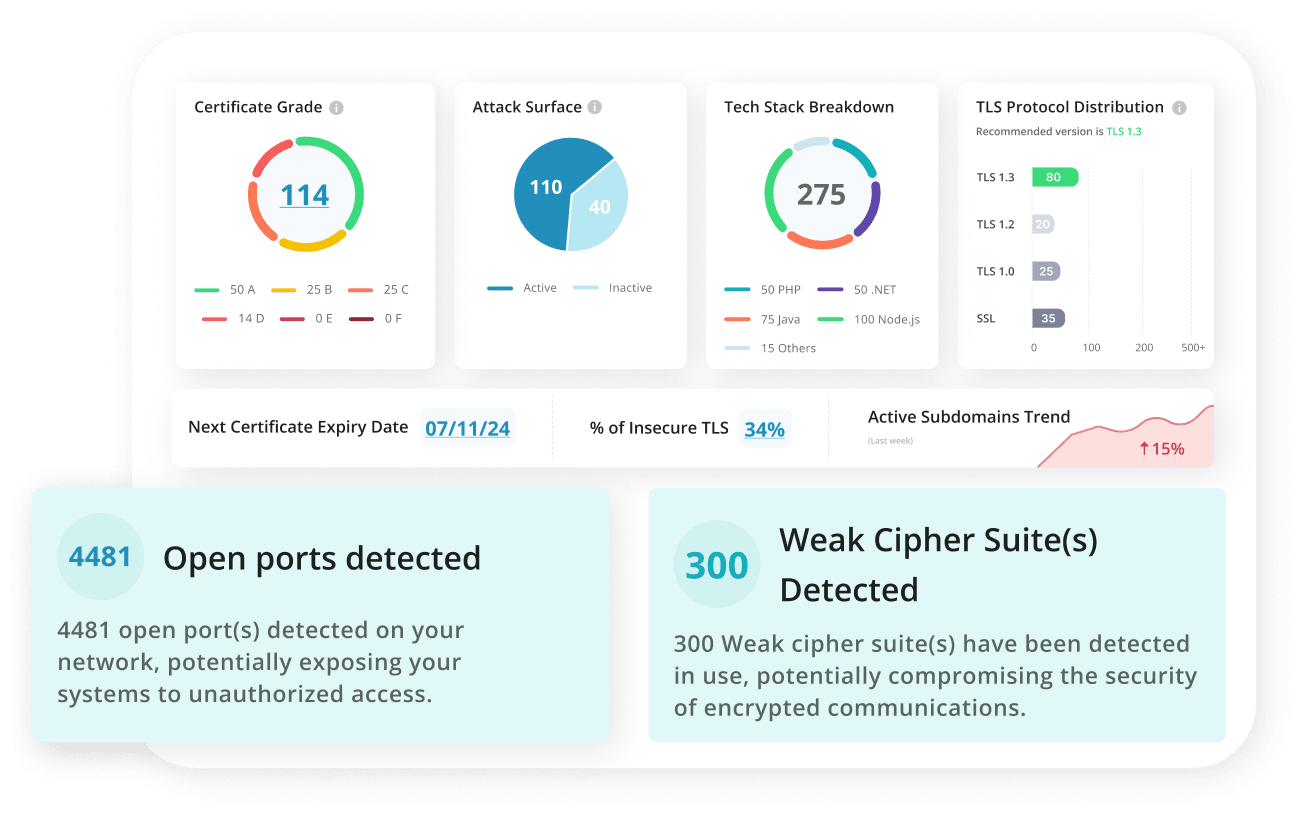
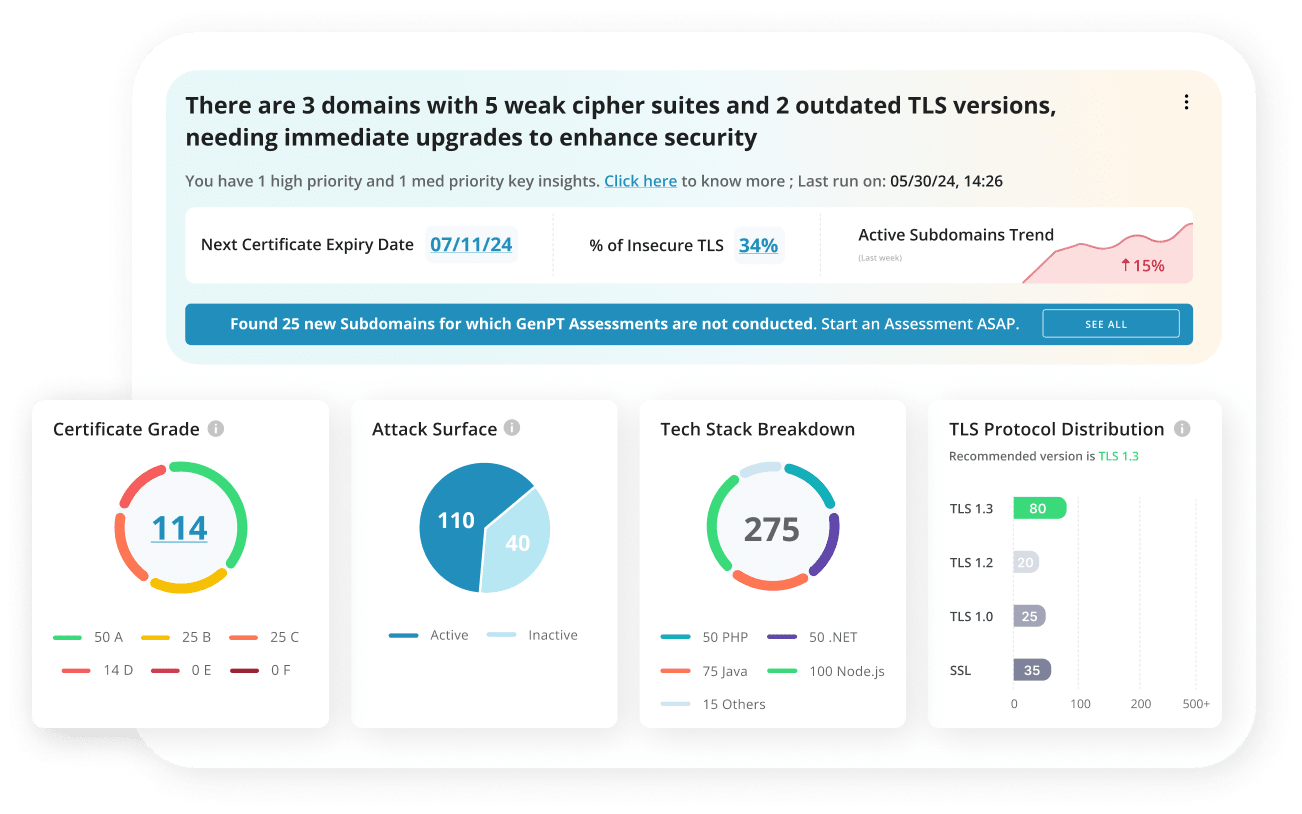
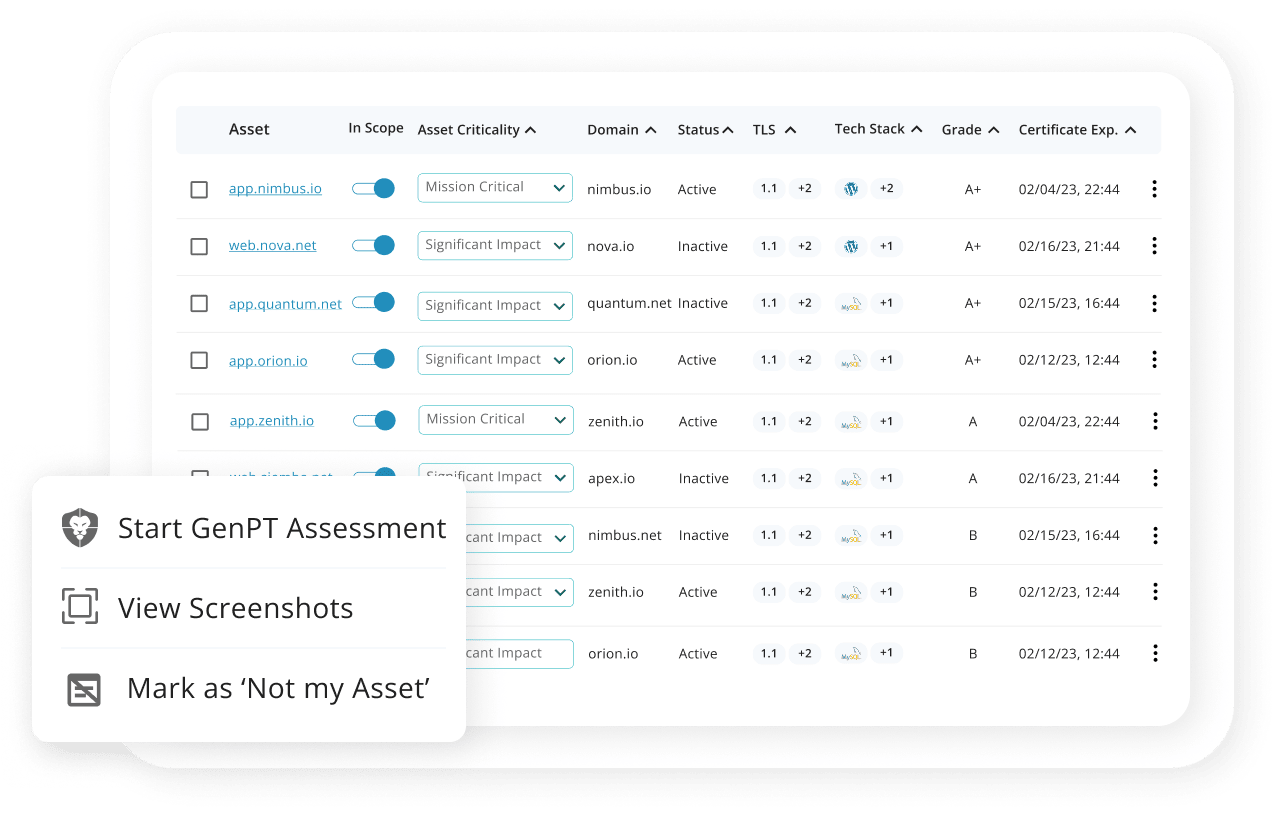
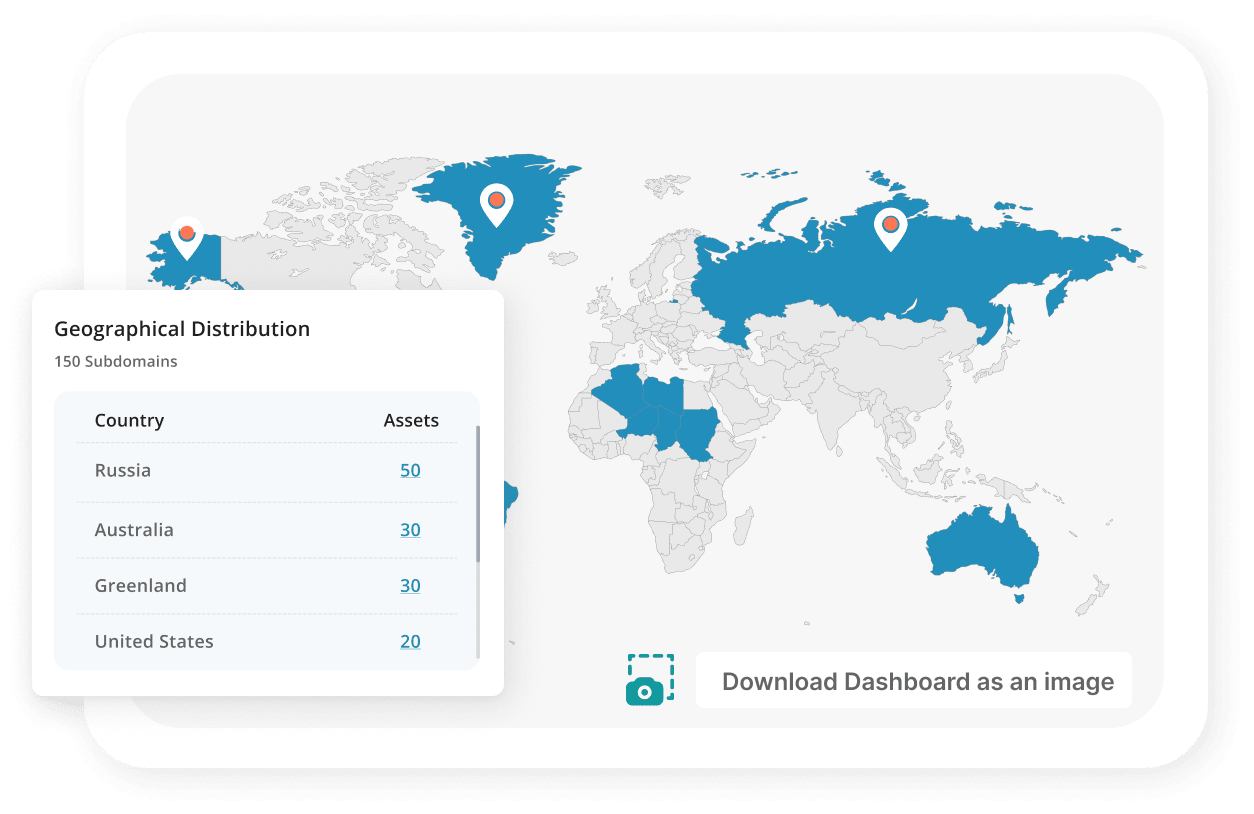
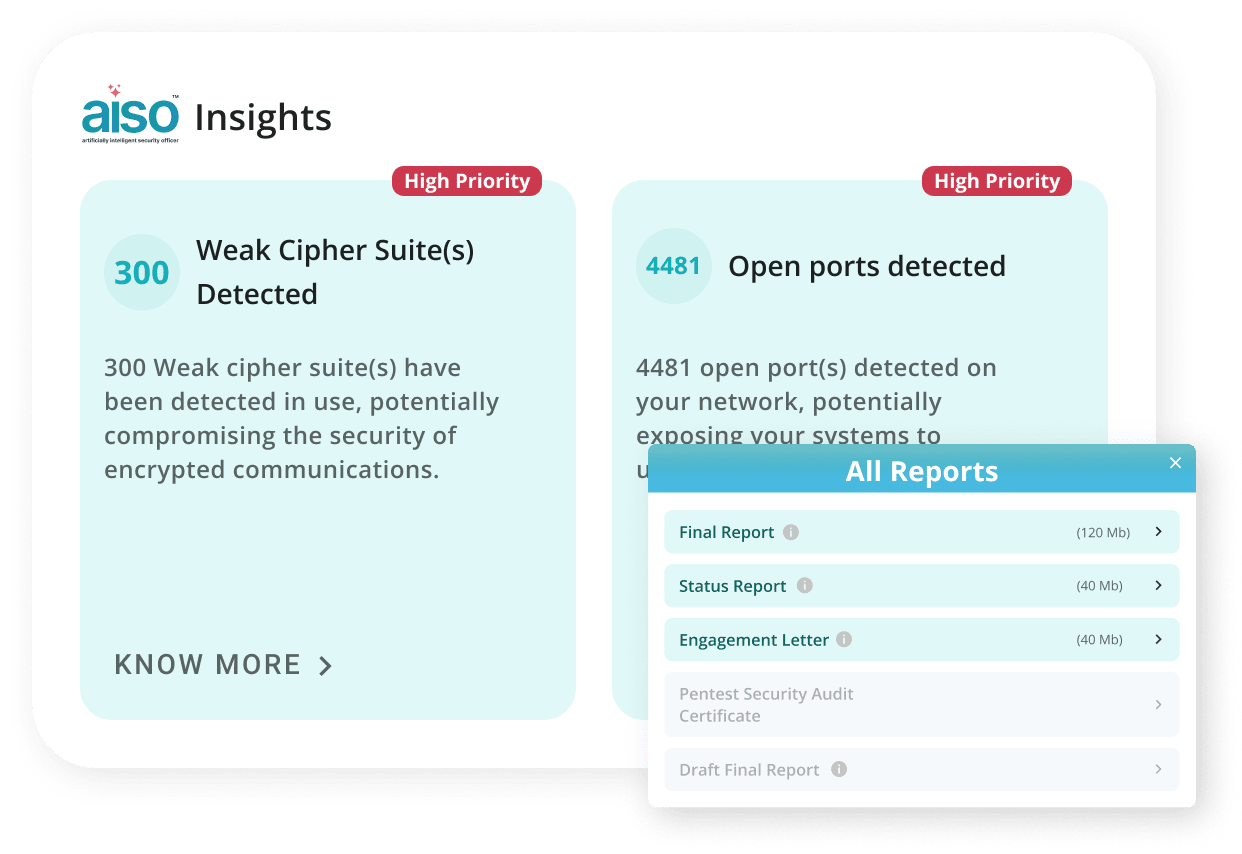
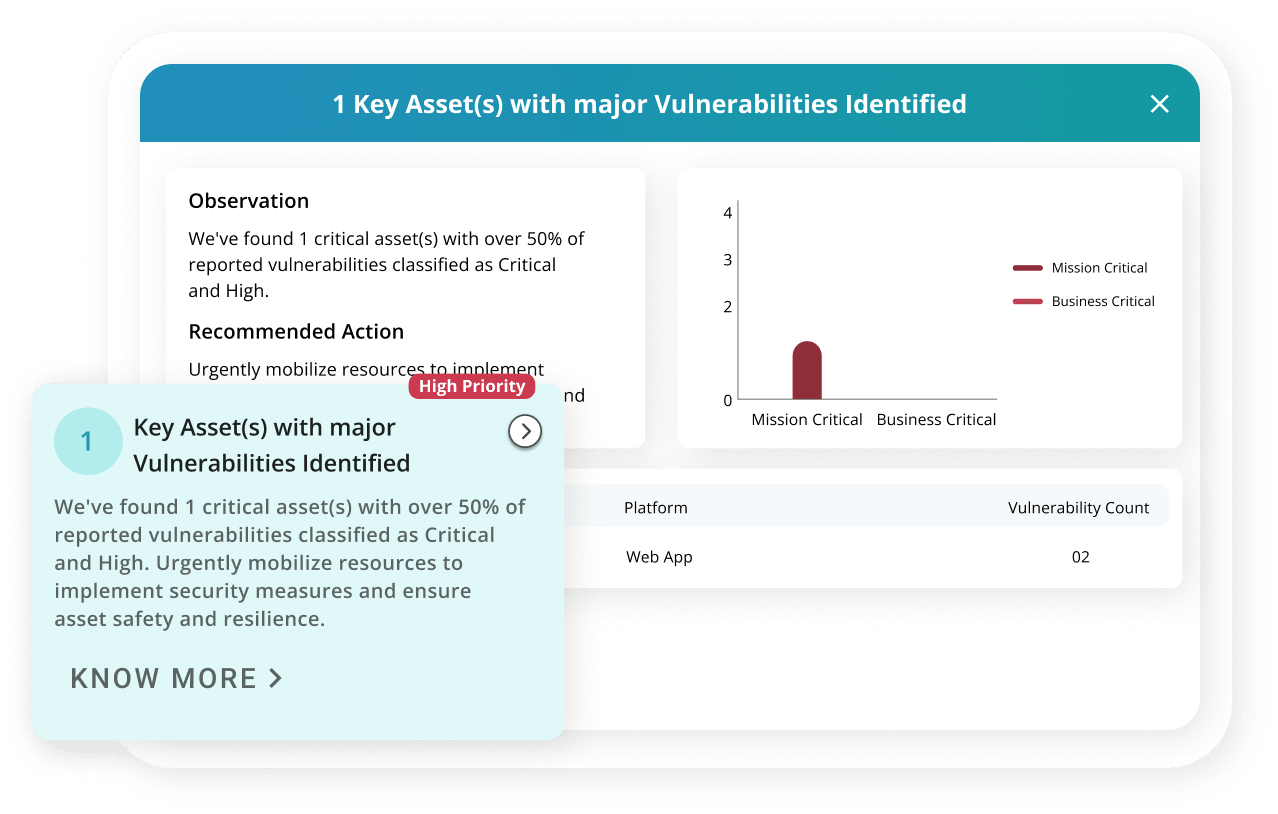
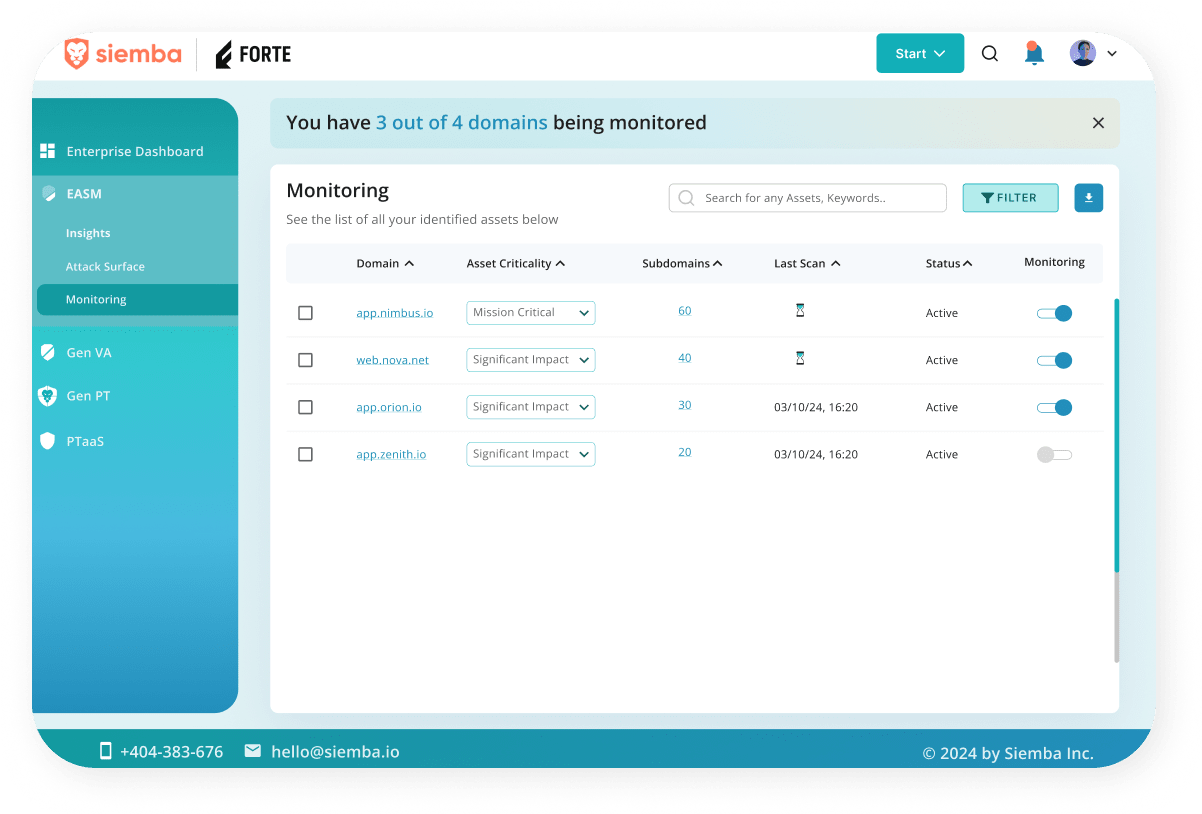
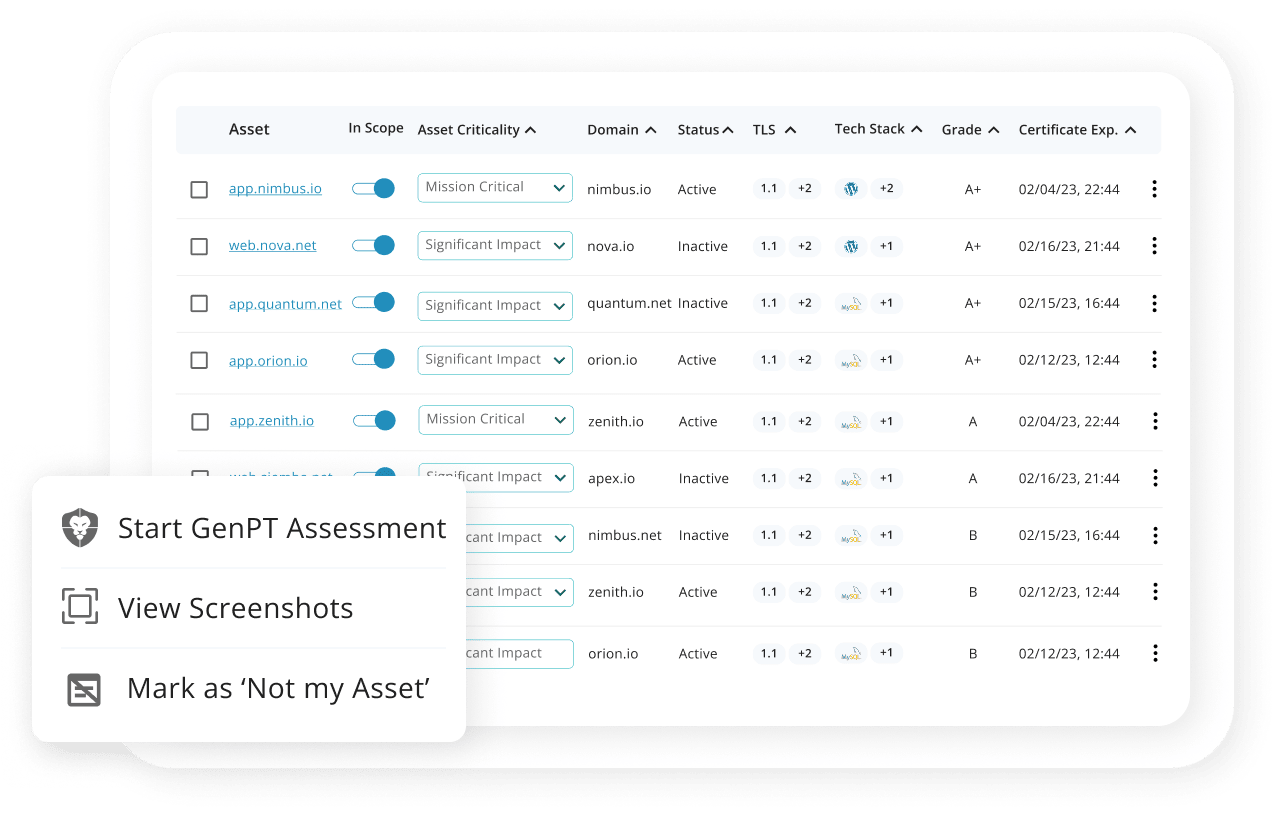
- Attacker’s Eye View
- Visual Dashboards
- Trigger Deeper Testing
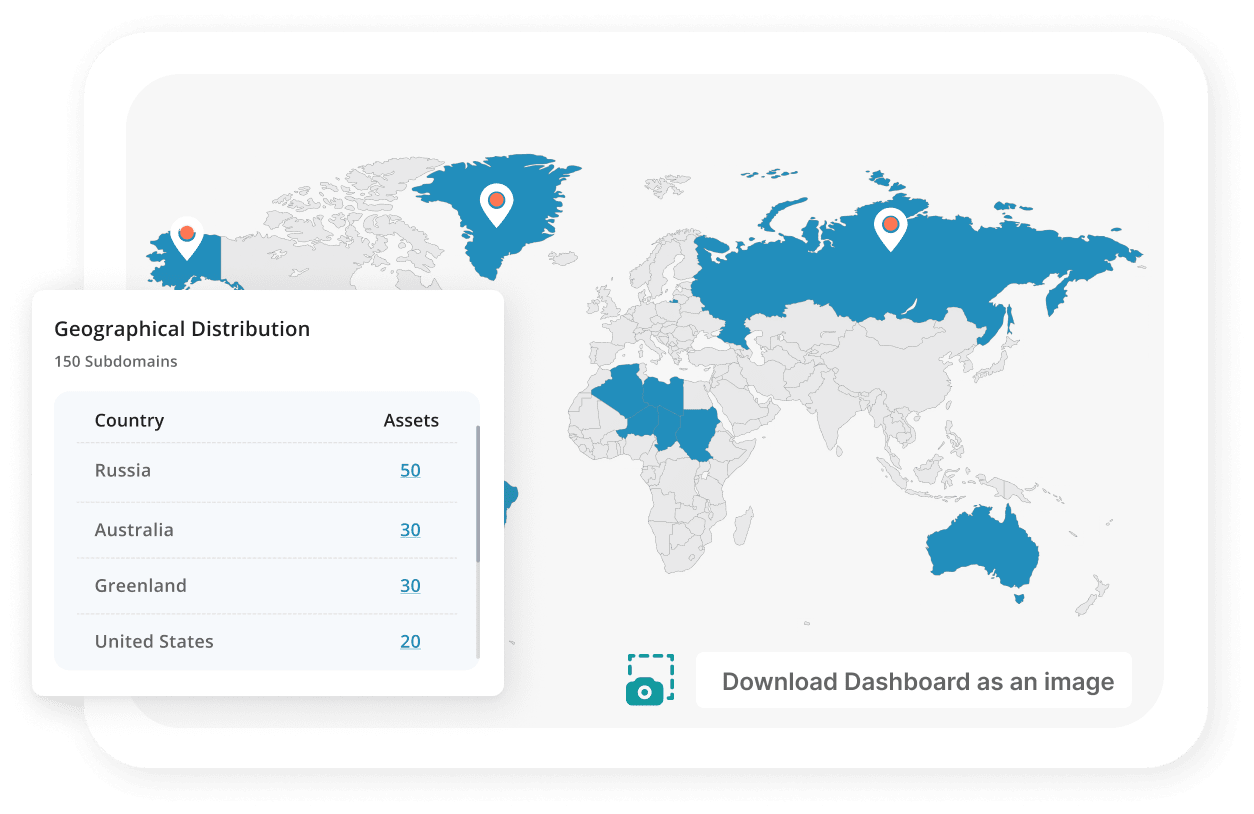
- Geo Mapping & Screenshots
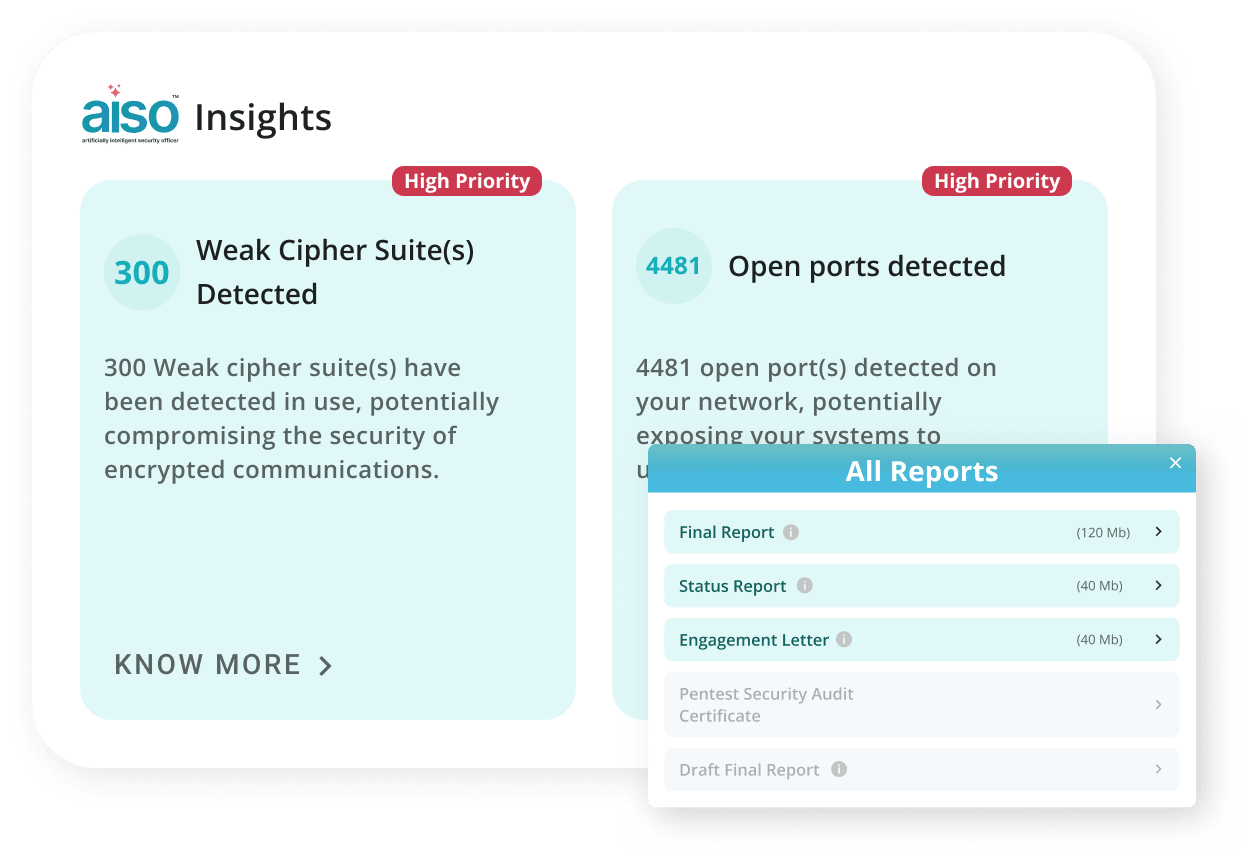
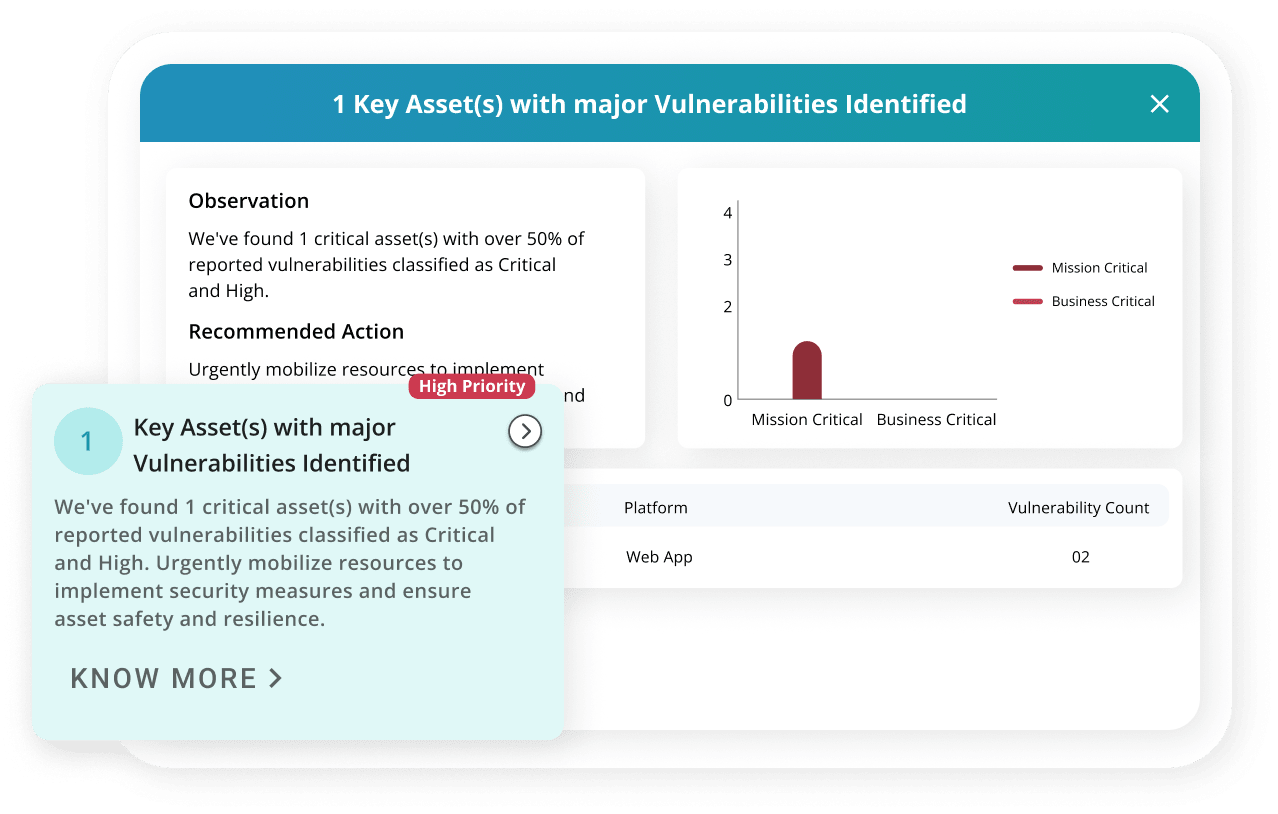
- Smart Reporting & AISO Insights
- Compliance Ready
- Custom Asset Scoping
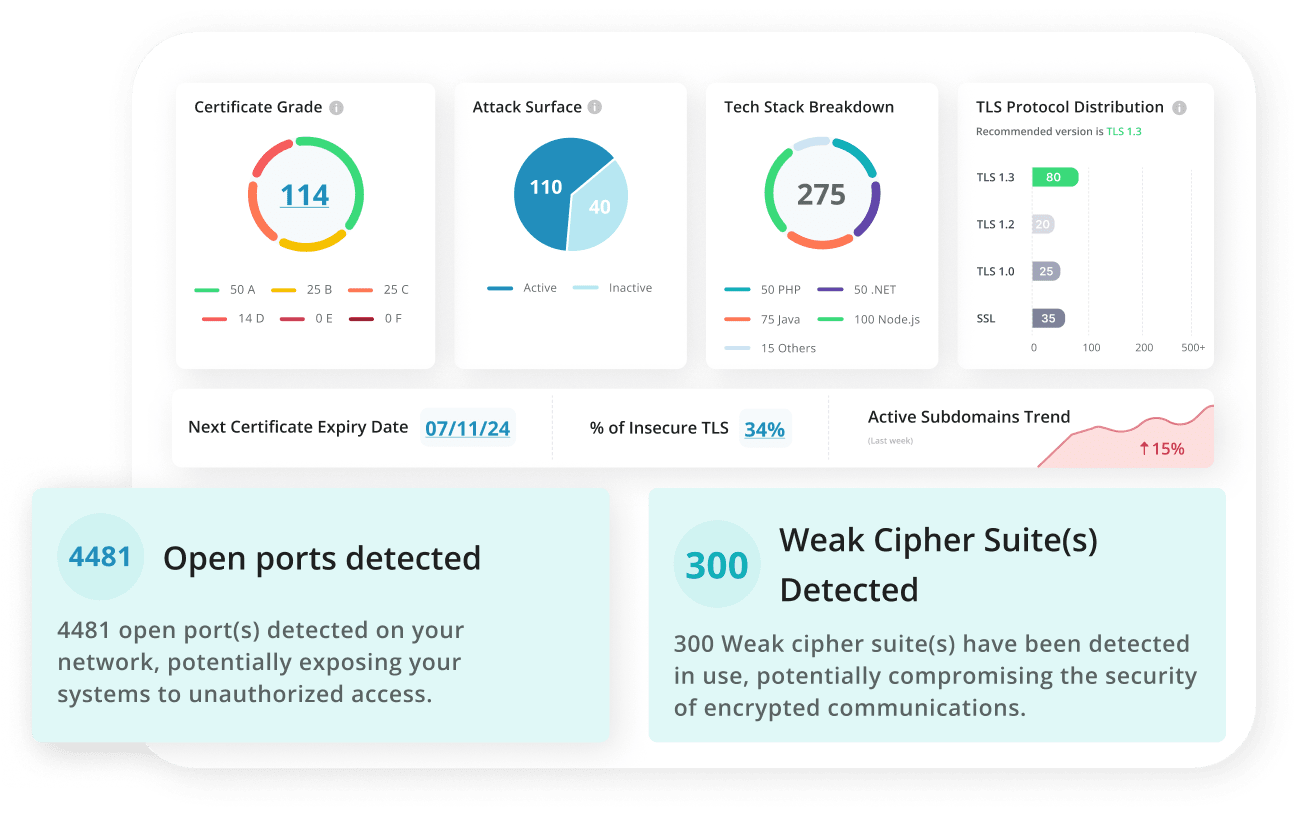
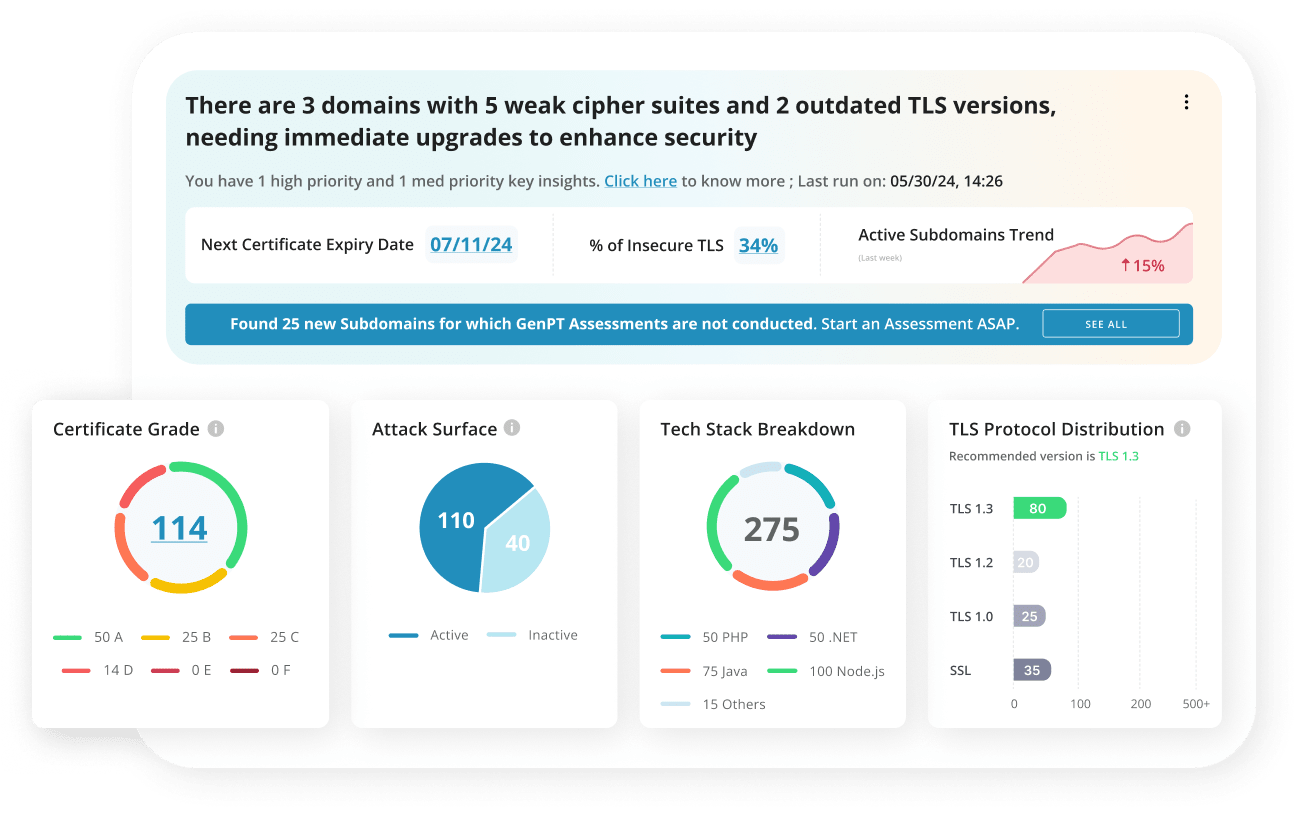
How Every Team Wins with EASM
From Dev to GRC, Everyone Benefits

Traditional Security Approaches vs. Siemba’s External Attack Surface Management (EASM)
Capability |
Traditional Tools |
Siemba EASM |
|---|---|---|
|
Discovery Method
|
Manual, credentialed, or network-bound
|
Non-intrusive AI-driven fingerprinting &
enumeration |
|
Monitoring Frequency
|
Point-in-time scans
|
Continuous monitoring with automated updates
|
|
Data Clarity & Context
|
Static spreadsheets and raw logs
|
Visual dashboards with TLS grades, domain trends,
and active/inactive mapping |
|
Remediation Readiness
|
Basic reports with no depth
|
Deep insights, action items, and instant DAST
triggering from asset view |
|
CTEM Integration
|
Standalone or siloed tools
|
Natively integrated with Siemba’s CTEM and AISO
for threat-driven decisions |
Protect What’s Public. Control What’s Exposed.
Siemba EASM gives you the visibility attackers hope you don’t have.
Always-on monitoring
Actionable insights
Integrated testing
Real-time, no-touch visibility
Start mapping your attack surface with GenVA
Explore Siemba's intelligent EASM platform in action





