Strengthen Your Security Posture with Enterprise Grade Penetration Testing as a Service (PTaaS)
.png?width=1118&height=750&name=Banner%20(5).png)
Reduce risk, monitor trends, and improve efficiency through continuous,
on-demand penetration tests that tackle a constantly evolving threat landscape. Tackle threats through real-time assessments and asset-level dashboards displaying critical findings and risks.
Trusted by













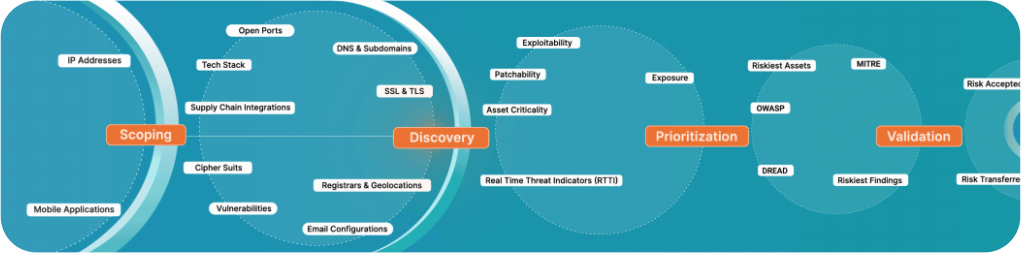
Siemba's PTaaS Moves at the Speed of Business, Without Breaking Things
Traditional Pentesting doesn't cover the entire attack surface leaving business-critical assets at risk. Our PTaas solution offers a mix of human & platform based pentesting to ensure complete coverage.
Trusted by






Prevent Attacks With Our Unified Platform and Expert-led Offensive Security
.webp)
-1.webp)
-1.webp)
.webp)
-1.webp)
.webp)
Transform Testing Into a
Well-oiled Machine
Build Proactive Security with AISO Insights
Stay Updated With
One-click Reports
Access a Team of Expert Ethical Hackers
- Get on-demand support for penetration testing, vulnerability assessments, and security audits
- Collaborate with experienced professionals to identify and mitigate vulnerabilities
- Access priority answers for questions asked on the enterprise dashboard
- Leverage the expertise of seasoned security professionals to address complex security challenges
Optimize Your Security Budget
- Visibility
- Scalability
- Insights
- Reporting
- Collaboration
- Cost Efficiency
Transform Testing Into a
Well-oiled Machine
.webp?width=1206&height=736&name=Transform%20testing%20into%20a%20well-oiled%20machine%20(1).webp)
-1.webp?width=1202&height=814&name=Bring%20clarity%20to%20chaotic%20processes%20(1)-1.webp)
Build Proactive Security with AISO Insights
-1.webp?width=1240&height=820&name=Build%20proactive%20security%20with%20AISO%20insights%20(1)-1.webp)
Stay Updated With
One-click Reports
.webp?width=1202&height=814&name=Stay%20updated%20with%20one-click%20reports%20(1).webp)
Access a Team of Expert Ethical Hackers
- Get on-demand support for penetration testing, vulnerability assessments, and security audits
- Collaborate with experienced professionals to identify and mitigate vulnerabilities
- Access priority answers for questions asked on the enterprise dashboard
- Leverage the expertise of seasoned security professionals to address complex security challenges
-1.webp?width=1202&height=814&name=Access%20a%20team%20of%20expert%20ethical%20hackers%20(1)-1.webp)
Optimize Your Security Budget
.webp?width=1202&height=814&name=Optimise%20your%20security%20budget%20(1).webp)
Powering Organisation-wide Security,
Role-by-role


Traditional Pentesting vs. PTaaS
Features |
Traditional Penetration Testing |
Penetration Testing as a Service (PTaaS) |
|---|---|---|
|
Visibility
|
Limited or no visibility; static reports shared
post-assessment |
Near real-time visibility with enterprise dashboards,
asset tracking, and centralized test views |
|
Repeatable & Scalable
|
Manual, time-consuming setup; difficult to
scale |
Automated test scheduling, bulk asset uploads,
and scalable testing |
|
Reporting
|
Basic, static reports with limited interactivity
|
Downloadable reports, real-time updates, and
deeper insights into findings and risks |
|
Insights
|
No insights; lacks proactive risk mitigation
guidance |
Threat and efficiency insights, emerging trends,
and proactive security measures |
|
Collaboration
|
Limited access to testers; formal, slow
communication |
Direct access to ethical hackers, on-demand
support, and expert collaboration |
|
Cost Efficiency
|
Expensive; requires external consultants
and manual efforts |
Reduces costs with automation, predictable
budgets, and continuous testing ROI |
Our Guiding Light
Our values aren’t just framed on a wall—they’re lived every day. They guide the hard decisions, the quiet work behind the scenes, and the way we show up, even when no one’s watching. These principles remind us why we’re here: to build something meaningful, together.
In The Spotlight
Defend Smarter. Choose Siemba.
Discover proactive defense at its best with our AI-powered full-funnel offensive security platform. Secure what matters most.
Success Stories From Our Clients
.png?width=380&height=378&name=image%20(58).png)
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Huno
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Success Stories
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Huno
Company, Designation
In The Spotlight
Build the Right Foundation for Your Penetration Testing Program
See Siemba's intelligent, autonomous PTaaS platform in action



