Trusted by













Siemba’s AI-driven DAST Proactively Mocks Autonomous Attacks to Prevent Real Attacks
Struggling to keep up with the ever-evolving threat landscape?
Leverage the power of Generative AI with Siemba's GenPT. Our AI-powered DAST engine autonomously identifies vulnerabilities before attackers do.
This issue in 60 seconds
-
What security leaders are seeing across the market and why it matters for 2026
-
A defining 2025 incident that reshaped how teams think about real risk
-
Why AI must push security beyond alert overload to contextual prioritization
-
Gartner’s validation of a major shift: Preemptive Exposure Management (PEM)
-
What we’re building toward and what’s coming next
-
Curated resources worth your time as you plan for 2026
Outages, Severity Flaws, and The New Big Shift
It’s the time of the year when we begin thinking about what we want our security posture in 2026 to look like.
And because cyber resilience dominates executive mindshare, the same questions keep echoing from the board room to SecOps and DevSecOps leaders: Where do you want to focus your budget, and what becomes the new priority?
At the same time, many organizations recognize that decisions made over the past year, often under time and resource constraints don't always age well. They leave behind gaps, inconsistencies, and legacy approaches continue to shape today’s risk in ways that are hard to ignore.

As 2025 wraps up, one thing is clear; the threat landscape is moving faster than ever.
AI is accelerating both attacks and defenses, while confidence in traditional approaches continues to weaken. Staying ahead now requires a more intentional look at strategy, sharper focus on real risk, and a willingness to rethink how exposure is managed.
The 2026 Security Landscape
3-Month Exposure Remediation
Gartner reports that enterprises can take up to three months to identify and address security exposures in AI-enabled applications leaving attackers a long window to exploit weaknesses.
Ransomware attacks to rise by 40% by 2026
QBE warns ransomware victims publicly named on leak sites will rise from 5,010 in 2024 to over 7,000 by 2026, marking a fivefold increase since 2020 and cementing ransomware as a persistent, large-scale threat.
Tool Sprawl Is Creating Blind Spots
Today, organizations manage an average of 17 security tools from five vendors, creating fragmented data and major context gaps. As a result, 97% of security leaders are prioritizing consolidation to reduce complexity and regain visibility.
Bigger Budgets, Lower Confidence
Despite rising security budgets, more than half of CISOs report low confidence in their security posture. As AI reshapes the threat landscape, leaders are prioritizing automation and continuous visibility over adding more tools.
Cloudflare's Widespread Outage
 So much has happened this year, especially in the past few weeks. Cloudflare was forced to cause a widespread outage on its own network to mitigate this critical, actively exploited vulnerability.
So much has happened this year, especially in the past few weeks. Cloudflare was forced to cause a widespread outage on its own network to mitigate this critical, actively exploited vulnerability.
But this self-inflicted network failure, which affected about 28 percent of HTTP traffic globally, was not a cyber attack.
It was “triggered by changes being made to our body parsing logic” while the company attempted to detect and fix the industry-wide flaw in React Server Components (RSC).
The seriousness of the threat forced this drastic measure. For the vulnerability itself, an insecure deserialization flaw carries a perfect CVSS 10.0 score, allowing unauthenticated Remote Code Execution (RCE) via a crafted HTTP request.
Most interestingly, within hours of its disclosure, the flaw was actively weaponized. China state-nexus threat groups, including Earth Lamia and Jackpot Panda, began active exploitation attempts and were even observed debugging exploits in real time against honeypots.
This unauthenticated RCE vulnerability in React Server Components and the forced global outage underscore the constant race between security providers and threat actors who quickly weaponize flaws in core open source components.
Cloudflare’s drastic action highlighted the extreme severity: one expert noted that if Cloudflare could not wait for a maintenance window, no organization running the affected React or Next.js versions should delay patching.
The quiet days are just rehearsal time. You either know you've been breached, or you soon will find out.
So what would you do if your company ran a significant portion of global internet traffic and had to choose between downtime or active RCE exploitation?
There will be varied explanations in the days ahead, but one truth stands out. Patching under pressure is not a viable strategy. Waiting for vendor patches or relying only on WAF rules is an unacceptable risk. We must shift from reactive fixes to more proactive, adaptable, long-term approaches.
2026 Imperative: AI Moves CISOs Beyond Alert Overload
Security teams are increasingly overwhelmed with alert overload caused by excessive findings from vulnerability scans. This results in wasted cycles spent on noise and false positives. Traditional prioritization that depends on static CVSS scores only makes this worse and leads to over-patching.

Siemba Co-founder & Chief Security Officer, Sandhya Prashanth highlights that this operational drag has become a major business hurdle.
The objective is not to discover more flaws but to identify the right ones. CISOs are now shifting to AI-driven contextual risk management, she explains, enabling teams to focus on high-impact threats rather than everything that appears.
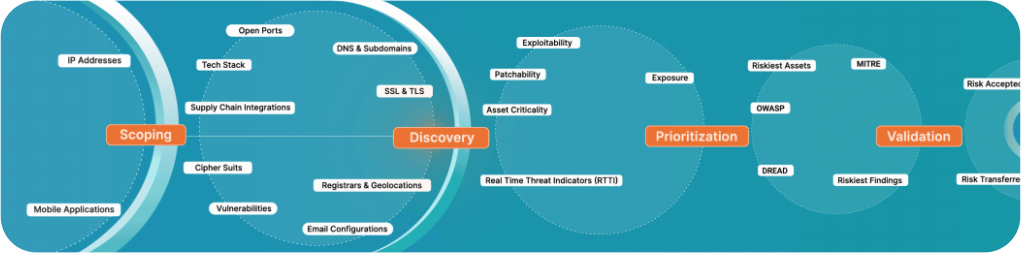
- The Full Stack CTEM Platform continuously identifies, prioritizes, and remediates threats across the attack surface.
- It acts as an AI-powered assistant for faster decisions, smarter prioritization, and automated threat response.
- Key capabilities include EASM (External Attack Surface Management) and GenVA (AI-driven Vulnerability Assessments).
Read Full Blog
The Paradigm Shift: Gartner Validates Preemptive Cybersecurity
The era of traditional proactive security is ending. As you plan for 2026, the new strategic focus is Preemptive Exposure Management.
Gartner has recognized and profiled the emerging technology of Preemptive Exposure Management (PEM) in its latest Emerging Tech Impact Radar. PEM is defined as a critical transition from generalized proactive defense to a targeted, intelligence-driven strategy for reducing exposure risk before exploitation occurs.
This validation reinforces Siemba’s vision that organizations must advance beyond static controls and adopt continuous, AI-enabled defense models.
Meet GenPT: One-Click AI-Native Security Testing
Stay Ahead with Application Security. Anywhere, Anytime.
The move toward PEM is accelerated by technology like our newly launched GenPT.
GenPT is Siemba's one-click, AI-Native automated security testing platform to simulate real-world attacks and identify exploitable gaps at scale. It dramatically improves speed and accuracy, especially when evaluating severity vulnerabilities.
Handpicked Reads
-
Prompt Injection Attacks: What They Are and How to Prevent Them: Link
-
The Business Case for PTaaS: Cost-Effective and Scalable Security Testing: Link
-
The Quantum Cybersecurity Revolution (via Forbes): Link
💡 Book Recommendation: A comprehensive view of cyber warfare and defense, arguing that cyberspace is now a primary battlefield. Link
Siemba Highlights
1. 5-Step Pre-Holiday Security Checklist (Free Download)
Cut through that noise and lock down your perimeter before the holiday freeze with a practical 5-step pre-holiday offensive security checklist.
2. Beyond The Checklist: Building Security Frameworks That Actually Work
A fireside chat where two seasoned leaders break down what actually makes frameworks scale and the early warning signs teams can’t afford to miss!
3. The 2026 Security Landscape Has Shifted. Are Your Assessments Keeping Up?
A complete playbook for planning, scoping, and executing 2026 security assessments.
“If you don’t know what you own at the start of the year, everything downstream becomes reactive.”
Watch the full webinar with Sandhya Prashanth (Co-Founder and Chief Security Officer, Siemba) and Kiran Elengickal (VP, Global Technology Alliances at Siemba)
Coming Soon: The Siemba Roadmap for 2026
We are continuously enhancing our platform for modern risk:
- API Testing (Coming Up)
Continuous testing for modern application stacks and API-driven services. -
New OWASP Restructuring
Updated vulnerability management aligned with the new OWASP categories. -
Enhanced Asset Management
Improved visibility and control of external-facing assets to reduce your attack surface.
Start Preempting for 2026
As you finalize your 2026 budget and security strategy, don’t wait for the next CVSS 10.0 flaw to drive action.
See how Siemba helps teams shift from reactive response to preemptive exposure management.
Siemba’s unified CTEM platform gives security leaders a complete view of their attack surface across applications, APIs, cloud, and vendors.
It combines AI-native instant security testing (GenPT) with strategic risk intelligence and prioritization (AISO) to help teams focus on what matters most.
The result: faster exposure reduction and confident, evidence-backed decisions.
Customers typically see value within hours, not months with measurable operational impact:
-
Up to 70% reduction in assessment and remediation costs
-
Around 90% time saved across security workflows
If you’re planning for 2026 and want fewer surprises, faster remediation, and clearer prioritization: Book a personalized demo or drop us a hello in the chat!
Our Guiding Light
Our values aren’t just framed on a wall—they’re lived every day. They guide the hard decisions, the quiet work behind the scenes, and the way we show up, even when no one’s watching. These principles remind us why we’re here: to build something meaningful, together.
In The Spotlight
Defend Smarter. Choose Siemba.
Discover proactive defense at its best with our AI-powered full-funnel offensive security platform. Secure what matters most.
Success Stories From Our Clients
.png?width=380&height=378&name=image%20(58).png)
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Huno
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Success Stories
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Huno
Company, Designation