ROAR - Edition 2

Start 2026 Strong: Security Assessment Templates & Checklists Inside!
Turn security chaos into a predictable plan for 2026
Trusted by













Siemba’s AI-driven DAST Proactively Mocks Autonomous Attacks to Prevent Real Attacks
Struggling to keep up with the ever-evolving threat landscape?
Leverage the power of Generative AI with Siemba's GenPT. Our AI-powered DAST engine autonomously identifies vulnerabilities before attackers do.
Editor’s Note
Hi there, and welcome to Edition 2 of Siemba’s ROAR Newsletter!
If you’re in security, chances are you didn’t plan to think about assessments this early in the year, yet someone has already asked for one.
A customer. An auditor. Procurement. A board member.
And suddenly, what should be a structured process feels rushed and chaotic.
This month’s edition is all about turning that moment into a plan so assessments stop being last-minute scrambles and start becoming predictable, manageable, and defensible.
Let’s dive in.
- Lavanya, Team Siemba
This edition helps you:
✔ understand what you own
✔ decide what to assess
✔ prioritize what to fix
✔ plan time and budget
✔ avoid last-minute security firefighting
Along the way, we’ve included practical templates and checklists you can reuse for:
• asset inventory
• assessment scoping
• remediation tracking
• annual assessment planning
The principle is simple: plan once, then execute steadily all year!
So…You’ve Been Asked for a Security Assessment
A security assessment answers 3 essential questions:
- What systems do we have?
- Are they vulnerable?
- What should we fix first?
In 2026, those questions matter more than ever.
Software ships faster than security can manually review. AI and LLM features introduce new attack paths.
Environments change continuously. Budgets are under scrutiny. Compliance expectations keep rising.
For many teams, the problem is not testing. It is planning. And yearly assessments are no longer optional.
They’re triggered by customer security reviews, audits, and procurement requirements, whether you’re ready or not.
What Turns Security Chaos into a Plan?
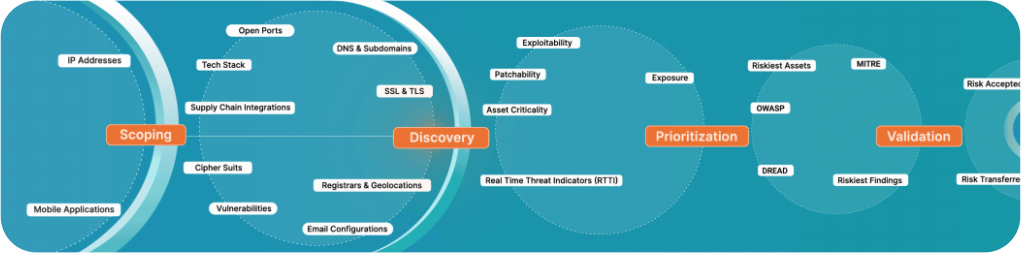
Every effective assessment program, regardless of company size is built on four foundations:
Asset Inventory → Scoping → Remediation → Ownership & Budgeting
We consistently see this structure used by mature security teams managing complex cloud and application environments.
These convert:
- last-minute audits into predictable execution
- vendor reports into actionable work
- security noise into measurable risk reduction
Security assessments today are also broader than many teams expect.
They include application testing, API and LLM testing, cloud configuration reviews, internal attack paths, and continuous validation. Annual vendor tests alone no longer reflect real risk.
Our assessment planning template helps teams map these different assessment types across the year instead of defaulting to one-off tests and hoping for the best.
Asset Inventory: Do you really know what you own?
Most environments grow quietly. Orphaned APIs, unmanaged cloud accounts, legacy systems, shadow IT, and systems without owners accumulate faster than teams realize.
When ownership isn’t clear, fixes slow down, retesting gets skipped, and audits turn into coordination exercises.
Mature programs maintain a current asset list, assign ownership to every system, track when each asset was last assessed, and tie findings back to the systems that produce them.
Each assessment must have an owner.
Each system must have an owner.
Each finding must have an owner.
Because you can’t secure what you don’t see, and you can’t improve what no one owns!
Our asset inventory and ownership template help teams establish this baseline without starting from scratch.
Scoping: What did you miss to test?
The Biggest Risks Live Outside Your Scope
Late surprises rarely come from what was tested. They come from what was not included.
Hidden dependencies, third-party systems, timeline mismatches, and missing environments are usually operational gaps rather than technical ones.
Teams that scale rely on consistent scoping approaches like clear checklists, tracked scope changes, and timelines aligned with engineering teams.
This reduces rework, improves predictability, and prevents assessments from becoming reactive exercises.
Good scoping is not about narrowing effort. It is about making risk visible.
That is why we’ve included a standard scoping checklist you can adapt for apps, APIs, cloud, and AI features.
Prioritization: Are you fixing the right things or just closing tickets?
CVSS scores are useful, but they don’t reflect business impact. Mature teams treat findings as risk items, not bug tickets.
The real question isn’t “How severe is this vulnerability?”, it is “What business harm does this enable?”
High-performing teams track coverage, remediation time, and repeat findings instead of just counting issues. This shows whether exposure is actually going down.
When prioritization improves, conversations shift from vulnerability lists to risk decisions.
Our remediation tracking template makes that measurable instead of relying on isolated examples.
Can You Prove Security Is Worth the Spend?
Planning fails when data is fragmented, effort isn’t visible, risk isn’t tied to spend, and ownership is unclear.
High-performing teams can answer:
• What’s being assessed?
• What’s open?
• What’s fixed?
• What’s next?
• What will it cost?
That turns budgeting from guesswork into planning.
How Long Can Spreadsheets Really Scale?
Yes, this can be managed manually.
But as environments grow:
• Spreadsheets drift
• Findings repeat
• Retesting becomes manual
• Risk loses context
Teams that scale centralize assets, scope, findings, remediation, and retesting into one operational loop.
This is the difference between tracking work and running a program.
Siemba is built to support that full loop without stitching together disconnected tools.
What Security Leaders Are Rethinking for 2026
Security leaders are shifting from isolated tests to continuous assessment models.
We see these shifts most clearly across SaaS, fintech, and cloud-native security teams.
They are assigning ownership for AI and LLM features instead of treating them as edge cases.
They are connecting assessment output directly to remediation workflows. And they are using data to defend security investment.
This shift is not driven by tooling but by operational maturity.
Exclusive - The Hidden Gaps in Planning Your 2026 Security Assessment Cycle
Watch the webinar session that discusses:
• asset visibility
• scoping discipline
• remediation planning
• impact based prioritization
• AI and LLM assessment ownership
• continuous assessment models
If You Only Fix One Thing This Month…
Validate your asset inventory and system ownership.
Then ask, "Can we run one assessment end-to-end from scope to fix to retest without disruption?"
If the answer is no, that is your 2026 starting point!
Resources and Planning Tools
To help you operationalize this, check out these detailed blogs:
These resources are designed to help teams move from reactive testing to structured assessment programs.
Ready to Make 2026 Your Most Predictable Security Year?
Centralize all your asset inventory, scoping, findings, remediation, and retesting in one platform with Siemba.
See how teams reduce risk, streamline audits, and track remediation in real time.
Book a demo to experience a complete security assessment loop with Siemba.
Our Guiding Light
Our values aren’t just framed on a wall—they’re lived every day. They guide the hard decisions, the quiet work behind the scenes, and the way we show up, even when no one’s watching. These principles remind us why we’re here: to build something meaningful, together.
In The Spotlight
Defend Smarter. Choose Siemba.
Discover proactive defense at its best with our AI-powered full-funnel offensive security platform. Secure what matters most.
Success Stories From Our Clients
.png?width=380&height=378&name=image%20(58).png)
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Huno
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Success Stories
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Huno
Company, Designation