GenVA: AI-Driven Vulnerability Assessments for Real Threat Visibility
.png?width=1124&height=767&name=banner%20(3).png)
Go Beyond Scan Results. See What’s Actually Exploitable.
Traditional vulnerability management throws endless lists at you. GenVA, Siemba’s AI-powered Vulnerability Assessment engine, flips the script to prioritize threats over noise. With deep threat insights, powerful AI correlation, and rich contextual data, GenVA helps you focus on the vulnerabilities that matter most, with speed and confidence.
Trusted by













GenVA Proactively Finds Vulnerabilities And Security Gaps in Your Environments
Stop relying on static reports and ad-hoc insights.
GenVA offers continuous, AI-powered vulnerability assessments, so you understand them and stay ahead of emerging threats.
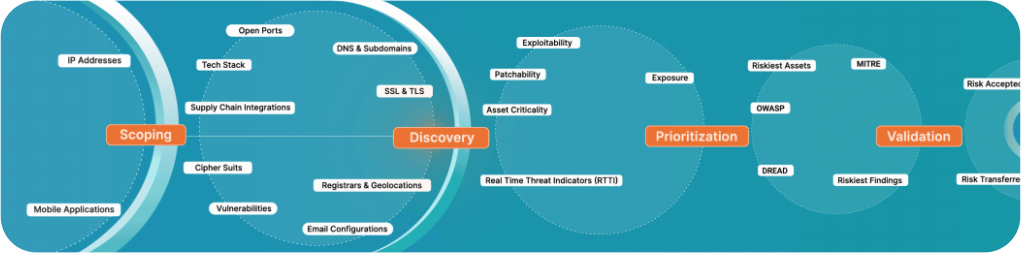
Why Traditional Vulnerability Management Falls Short
Stop Managing Vulnerabilities. Start Eliminating Threats.

Why Traditional Vulnerability Management Falls Short
Stop Managing Vulnerabilities. Start Eliminating Threats.



Feature-Packed and Purpose-Built
Everything You Need for Smart, Scalable Vulnerability Assessments
-1.webp)
.webp)
.webp)
.webp)
.webp)
-4.webp)
.webp)
- AI-Driven Threat Insights
- Efficiency Insights
- Powerful Scan Controls
- Smart Finding Grouping
- Exploit & Patch Awareness
- One-Click Reporting
- Compliance Framework Mapping
-1.webp?width=1258&height=814&name=AI-Driven%20Threat%20Insights%20(1)-1.webp)
.webp?width=1276&height=814&name=Efficiency%20Insights%20(1).webp)
.webp?width=1202&height=814&name=Powerful%20Scan%20Controls%20(1).webp)
.webp?width=1202&height=814&name=Smart%20Finding%20Grouping%20(1).webp)
.webp?width=1266&height=814&name=Exploit%20%26%20Patch%20Awareness%20(1).webp)
-4.webp?width=1296&height=814&name=One-Click%20Reporting%20(1)-4.webp)
Built for Every Team. Aligned With Your Security Goals.
How Your Team Gets More Done with GenVA

What You’re Using vs. What GenVA Delivers
Capability |
Traditional Vulnerability Management |
GenVA by Siemba |
|---|---|---|
|
Threat Prioritization
|
Severity-based, lacks exploit correlation
|
AI-driven threat insights prioritize by exploitability and
business impact |
|
Noise Reduction
|
Endless alerts and duplicates
|
Smart grouping by threat level, status, asset
criticality, and confirmation |
|
Reporting & Insights
|
Static reports, minimal context
|
One-click reports with CVSS, DREAD, CWE,
business risk, and remediation guidance |
|
Scanning Control
|
Limited scan profiles and frequency
|
Custom scan profiles, recurring schedules, and
granular control |
|
False Positive Management
|
Manual review and triage
|
Automated grouping and easy status toggling
(false positive, retest, reopened) |
|
CTEM Integration
|
Standalone platform
|
Native to Siemba CTEM for continuous threat
exposure visibility |
Built for Every Team. Aligned With Your Security Goals.
How Your Team Gets More Done with GenVA
Our Guiding Light
Our values aren’t just framed on a wall—they’re lived every day. They guide the hard decisions, the quiet work behind the scenes, and the way we show up, even when no one’s watching. These principles remind us why we’re here: to build something meaningful, together.
In The Spotlight
Defend Smarter. Choose Siemba.
Discover proactive defense at its best with our AI-powered full-funnel offensive security platform. Secure what matters most.
Success Stories From Our Clients
.png?width=380&height=378&name=image%20(58).png)
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
.png?width=380&height=378&name=image%20(58).png)
Huno
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Success Stories
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex Chriss
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Alex
Marko, Ceo
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
John
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Juliya
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Huno
Company, Designation

.webp?width=1202&height=814&name=Compliance%20Framework%20Mapping%20(1).webp)


